In today’s ever-evolving digital landscape, it’s becoming more and more difficult to stay safe online from cybercriminals.
It the second half of 2022, The Office of the Australian Information Commission (OAIC) reported that 350 data breaches were the result of “malicious or criminal attacks”, which makes up 70% of all data breaches, a rise of 41% from the first half.
Hackers today employ sophisticated techniques to bypass security measures, and their attacks have become more targeted and intelligent. We explore some of the techniques used:
Phishing
A deceptive cyber-attack where scammers impersonate trusted sources to trick individuals into revealing sensitive data. A hacker will pose as a trustworthy party and send a fraudulent email or text message, hoping you will voluntarily reveal your personal information such as login credentials or financial details. Sometimes they lead you to fake "reset your password" screens; other times, the links in the email will install malware on your device.
Tip: It is vital to be cautious when you receive a suspicious email or message. Never enter your password into a website unless you are sure it is legitimate. You should also avoid clicking on links in suspicious emails, and instead go directly to the website in question by typing the address into a website browser. It is also important to use security measures like multi-factor authentication to make it more difficult for attackers to successfully guess a password. It’s also a good idea to ensure your computer’s antivirus software is up to date, and that your smart phone software is updated regularly too.
Brute force attack
One of the most common methods used is brute-forcing weak passwords. By using automated tools, hackers can rapidly try various combinations until they crack the code, granting them unauthorised access to sensitive accounts. According to onelogin, a hacker can try 2.18 trillion password/username combinations in 22 seconds and if your password is simple, your account could be compromised.
Tip: Be sure to use strong and unique passwords. Enabling two-factor authentication can also provide an additional layer of protection.
Man-in-the-Middle attack
Scammers can intercept and relay communication between two parties without their knowledge. This allows the attacker to eavesdrop on sensitive information or modify the communication to their advantage.
Tip: It is important to be cautious when sharing sensitive information, and to verify the identity of the other party before disclosing any sensitive data.
Cyber incident breakdown (July – December 2022)
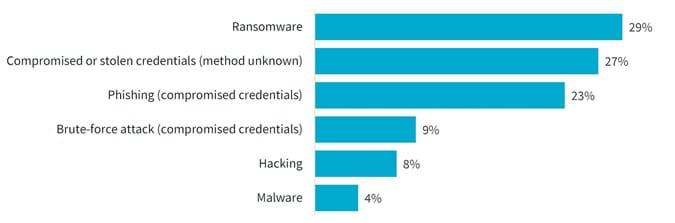
Source: oaic.gov.au
Recent data breaches and their impact
Data breaches have demonstrated the catastrophic consequences of cyber attacks on countless individuals and businesses alike. It can cause financial loss, identity theft, reputational damage, exposure to personal information and emotional distress. Here are some recent examples and their implications for affected customers (according to UpGuard):
Latitude
Latitude, the Australian personal loan and financial service provider, was affected by a data breach that impacted over 14 million people from Australia and New Zealand in March of 2022. The Latitude breach was one of Australia’s largest breaches in recent history.
The attack occurred when one set of employee credentials was stolen, allowing access to Latitude’s customer data, mainly consisting of: names, birth dates, physical addresses, email addresses, phone numbers, driver’s license numbers and passport numbers.
Optus
Australia’s second largest telecommunications company, Optus, experienced a data breach in September 2022 which was one of the biggest security breaches ever in Australian history.
Cybercriminals breached Optus' internal network, compromising personal information and impacting up to 9.8 million customers, almost 40% of the population.
Personal data included in this compromised data set included: names, birth dates, addresses, phone numbers, passport information, driver's license numbers, government ID numbers, medical records and Medicare card ID numbers.
It is believed that this was an extremely sophisticated attack that circumvented the company’s strong cyber defenses.
Medibank
In December 2022, Medibank, the Australian health insurance company, was the victim of a major data breach, affecting the personal details of 9.7 million customers. The attack was believed to be linked to a well-known ransomware group based in Russia.
The privacy breach was first discovered when the attackers posted on a dark web blog, a folder that contained a small amount of data samples, indicating that they had larger amounts of data to release, and demanded a $10 million ransom. The data included: names, birth dates, passport numbers, medical claims data and medical records.
Service NSW
In April 2020, 47 Service NSW staff had their email accounts compromised through a series of phishing attacks. This led to 5 million documents being accessed, 10% of which contains sensitive data impacting 104,000 people.
A major contributing factor to the seamless breach was the lack of multi-factor authentication.
Summary
Though these examples are some of the biggest breaches, no individual, company or sector, big or small can be considered safe.
Hackers are indeed becoming smarter, and these breaches may not be in our control, but that’s why members are encouraged to remain vigilant and focus on safeguarding the aspects within their control.
By maintaining strong password security, you can protect yourself against potential breaches. This small effort can make a significant difference in keeping your finances safe and secure.
If you suspect that your bank account has been compromised or you don’t recognise a transaction on your account, please contact us immediately on 13 61 91.
Sources:
https://www.geeks2u.com.au/geekspeak/the-changing-face-of-online-scams/
https://www.smartcompany.com.au/opinion/hackers-targeting-marketing-team/
https://www.oaic.gov.au/privacy/notifiable-data-breaches/notifiable-data-breaches-publications/notifiable-data-breaches-report-july-to-december-2022
https://www.upguard.com/blog/biggest-data-breaches-australia
https://mojoauth.com/blog/password-attacks/
https://expertinsights.com/insights/the-8-most-common-types-of-password-attacks/
https://www.onelogin.com/learn/6-types-password-attacks






